The popular ways of hiding your IP and identity are VPNs, proxies, and the TOR browser. One is better than the other— in different scenarios and for different requirements. But probably your identity is already “somehow hidden” but you might don’t know how or why. Or vice versa, you might think you are protected using an anonymity method, but you are really not. Before you go for one method or the other, let’s find out why you would need to hide your IP. And why would someone track down your IP and how could they do it? In this post, we’ll go through the “truth about hiding your IP” – an advanced version. We’ll discuss IP, Network Address Translation (NAT), tracking down your IP, ways to hide your IP, and the importance of the no-logs policy.
Private vs Public IP, and why NAT is key.
IP is an Internet (or network) identifier. When you use any Internet service, website, messaging app, streaming service, you are using a source public Internet Protocol (IP) address and a destination IP to exchange messages. This is much like a post mail, you have a “From” home address and a “To” destination address. There are public and private IPs. A private IP is used within private networks, usually behind an Internet gateway. Public IPs are global addresses used for Internet addressing.
When you are in your private network and request a service (web, file transfer, VoIP, P2P) from a distant server, your public IP address will be the unique Internet identifier that differentiates you from the rest of the world. And, the Network Address Translation (NAT) protocol is the one, doing those translations. Let’s use the following picture to explain this concept.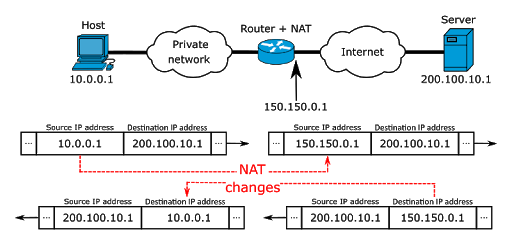 The Host (10.0.0.1) is behind a “Private Network” so it is using a private (source) address. If the “Host” wants to use the Internet, it needs to use an Internet gateway or “Router with NAT”. The target “Server” (web server, email, FTP, etc) with public IP 200.100.10.1 uses the router’s interface public IP (150.150.0.1) which is considered an “Internet exit node” to communicate across the Internet.
The Host (10.0.0.1) is behind a “Private Network” so it is using a private (source) address. If the “Host” wants to use the Internet, it needs to use an Internet gateway or “Router with NAT”. The target “Server” (web server, email, FTP, etc) with public IP 200.100.10.1 uses the router’s interface public IP (150.150.0.1) which is considered an “Internet exit node” to communicate across the Internet.
The importance of NAT.
Network Address Translation (NAT) is a protocol used worldwide to help reuse blocks of reserved IP addresses in order to avoid IPv4 address exhaustion, and can be also useful for security— as it maps private to public IPs. So, if you are one of the “clients” behind a large private network (NAT) with dynamic IP addressing (DHCP), mapping back to your source IP would be very difficult. Dynamic NATed Gateways are a common practice nowadays, especially with network mobile carriers, as they are trying to reuse or recycle public IPs.
Tracking down your IP

Anyone with your IP address could easily know “at least” what region and country your IP is coming from. The reason is: IP address “numbers” are broken down into regions known as RIRs (Regional Internet Registry). RIRs will allocate their IPs to National Internet Registries (based on countries), NIRs, Local Internet Registries (LIRs), or Internet Service Providers (ISPs). But can they go further than country and region? could they know your ISP, town, or home address? Yes, it is possible.
There are IP geolocation services that attempt to map a public IP address with a physical address. They take data that associates your IP (or subnet) to a location, for example, weather station, connection speed, ISP, domain name, time zone, etc.
Why and how would someone track down your IP? And what can they do with it?
For the most part, websites and web services are interested in knowing where their incoming traffic is coming from. This interest could be for various reasons, including, marketing, advertisement, or copyright protection. For example, a website might want to tailor its language to suit your visit or show you specific ads. Or a streaming service such as Netflix might show you a completely different library with content that is suitable and lawful to display in your region. Government agencies might also want to track down the activities and IPs in torrent swarms to avoid illicit downloads, or even track IPs on the dark web to solve cybercrimes.
How should you hide your IP?

By default when you browse the Internet, you will be already using your router’s IP (Internet exit interface). Or in the case of a smartphone, you’ll likely be behind a carrier-grade NAT (not local NAT). The mobile core network’s gateway will be handling User Equipment (UE)’s IP private to public mappings. So, the idea of hiding your IP should be:
- Masking your IP with someone else’s IP, and using it as an Internet relay. In the case of a VPN, the encryption does not hide your IP, but your data. It is the VPN server that hides your IP behind its own.
- Taking that Internet exit node, as far and through as many hops as possible, without compromising speed.
When you hide your IP, you guarantee that destination services including torrent swarms, streaming services, websites, etc, do not see your source IP.
Popular ways to hide your IP?

Proxy
A proxy acts as an intermediary between you (source IP) and the destination. The proxy receives your request and uses its IP to forward it. Proxies also perform some actions, such as ensuring encryption (SSL Proxy), changing HTTP headers (Anonymous HTTP proxy), or even introducing authentication (SOCKS5). Two good methods for hiding IP with proxies are using proxy chains (various proxies simultaneously) or Rapidseedbox’s IPv6 proxies which are popular nowadays.
VPN
Virtual Private Networks (VPNs) are another popular way to hide your IP. The best VPNs were designed to “virtually” extend and connect two distant networks. Most of the time these networks are connected using the Internet public network, so they use encryption mechanisms to make data unreadable by anyone intercepting the traffic. When you browse the Internet via a VPN, you are using the VPN server’s IP to hide behind.
TOR
The Onion Router (TOR) is another popular method to hide your IP. TOR uses a massive network of (volunteer) relays to forward traffic. It takes your traffic through a “random” path of these relays and exits via an exit node with encryption.
Two of the most popular ways (VPNs and Proxy) will likely have you dealing with a provider. A provider is the only one that could potentially map your source IP to a destination IP. That is why a no-logs policy is crucial.
Who is logging your traffic?

If you are inside a large corporation (or using a public WiFi), your connection might be already being filtered and logged. Your local ISP might also be filtering and logging your Internet traffic. If you are browsing the Internet without any kind of proxy or VPN, the ISP’s firewalls on the way to your destination will, most likely, inspect and filter your traffic. Your local ISP, which is providing you an exit connection to the Internet, could also be collecting and storing logs if required by law. See the Five Eyes Alliance.
Why is the no-logs policy so important?

When you mask your IP with someone else’s, such as a Proxy or VPN server, your ISP will still see your traffic, but it will be destined to a single destination (and encrypted in the case of VPN). Plus the destination server will only see the VPN or proxy server’s IP, and not yours. Still, the proxy or VPN service providers know your source IP and destination IP, and could be storing your traffic logs. Logs could include usage logs or connection logs, including timestamps, used bandwidth, sour-destination, IP addresses, or browsing data. The no-logs policy is so important because it explains to the user how a provider is dealing with their data. What type of data are they storing and for how long.
Final verdict
The more you bury your source IP— the better
If you can have a proxy or VPN server to send your Internet requests to, let it forward requests for you, and receive the replies. This kind of “middle-man” buries your source IP. The more “middle-mans” (proxies, VPN server, TOR server, etc) the deeper you can hide your IP, but the more your speed will be compromised.
Encryption adds strong privacy
To avoid getting your traffic data intercepted by WiFi hackers, the IT department, your ISP, or your Government, use strong encryption.
No one can be fully anonymous
If you are not behind a proxy or VPN, learn about the data laws in your country, as they directly affect how your ISP handles logs. If you use a proxy or VPN, ask them how they are handling your traffic logs.







